FORT LEE, Va. –
From extortion and phishing to identity theft and hacking, cyber criminals target personal information with innovation and variance. In today’s online world, digital security protects more than bank account numbers. Much of everything is captured on the internet. An understanding of threats and how to protect against them remains vital.
Tobi Beck serves as the chief of strategy, planning, and governance with Defense Contract Management Agency’s Information Technology Directorate. In this computer-safety series, experts share tips to stay safe online. Today, Beck explains the first rule to avoid internet scams.
I love shopping online. It’s great being able to avoid the hassles of driving and crowds of people. Plus, the selection is often better than most brick and mortar stores. I also like the convenience of digital receipts sent directly to my email because they are easier to file, particularly for deductible tax items.
But often, with convenience comes risk. In this case, the convenience of getting an electronic receipt requires the risks involved with handing my email address out to companies.
Normally, those email addresses are stored under lock and key, and only used by businesses for official purposes. But most businesses also offer ways to sign up for emailed advertisements about promotions and upcoming sales. This is where paying attention to the fine print of what you’re signing up for is important. The terms and conditions will normally explain whether your email will be used for just internal ads or if they will also share your email with other companies.
That last category is like a camel’s nose under the tent. It’s the doorway to a much larger problem.
When your email is shared with other vendors, they will also have a copy in their database, and they may share your email with even more vendors. Each additional database of emails must be protected or there is a risk of your email address being used by a scammer.
Once in the hands of these unscrupulous users, your address becomes up for grabs by anyone. Suddenly you are getting emails from Nigerian princes and about the latest tinnitus cure and diet miracle drug. You are a valuable asset to scammers. If they can get information from you, they will. Even your email address is worth something when sold as part a list.
Scammers take advantage of the convenience of online shopping, subscriptions, auto-renewals and email lists. If your email is sold to a criminal list, you could be sent some fairly clever scams.
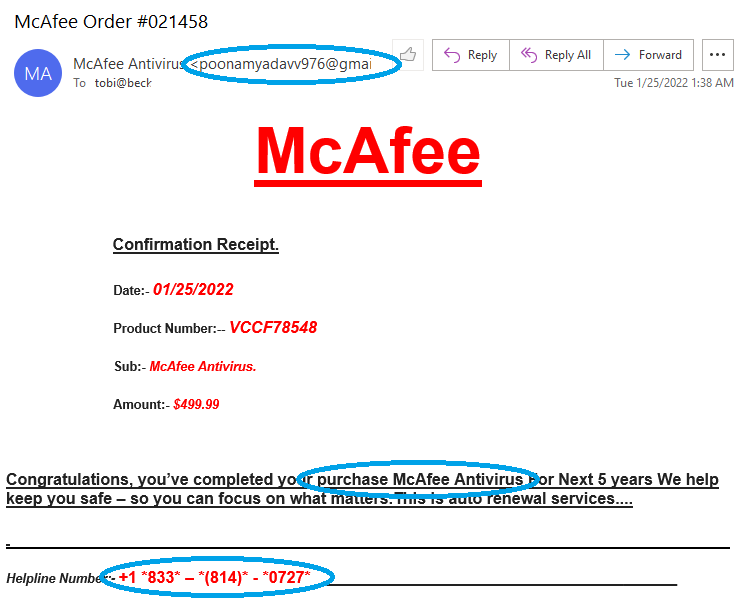
The sample email above, which I received recently in my inbox, is an example of one of these scams. Thankfully, there were several things present in the email that helped me determine that this was a scam right away.
First, I don’t use McAfee — but lots of people do, so this may not alert them. This scam in other varieties uses common financial institutions. I once received similar emails listing purchases I made from Wells Fargo, Bank of America and US Bank — all in the same afternoon — with instructions to reply immediately if a purchase they recorded was not legitimate. All three had the same misspellings and poor grammar.
But let’s assume that you do use McAfee anti-virus software. You may say to yourself, “Hey, I didn’t purchase this, and I don’t have $499 to just lose. I’m going to dispute this.” So you write back and explain that you did not buy this. But look closer, who is that email going to?
The email address Poonamayadavv976@gmail.com is probably not going to the McAfee. Anything going to McAfee has an email that most likely ends with something like “mcafee.com.” If you’re unsure what an official email from a company looks like, you can always visit the company’s website and look for a customer service email listing. However, never click on a link inside an email that says it goes to the official website or to the customer service department, it doesn’t. It will go to the scam artist who will be happy to take your money.
Another thing to notice in the scam email is that virus software is not that expensive. You can purchase a subscription to most any quality virus software from around $35 to $150 a year. On a side note, as an information technology professional, I can say that owning virus software is usually a good investment for your personal computer as it will block most known computer viruses and offer backup protections.
Next, look at the wording in the email. Many times scam emails contain obvious errors like misspellings, incorrect grammar or missing words. In this example, they left out the word ‘of,’ and it is a fairly good indicator that the person who wrote it may not speak English as a first language and most likely does not work in the customer support section of a software company.
Finally, look at how the phone number +1 is an indicator that you are placing a call overseas. McAfee, a US-based company, is unlikely to have a US-based customer call overseas for customer support. Next, note how the phone number is written. It’s not written in the standard US format. The brackets are in the wrong place, and unnecessary asterisks are present.
Asterisks are used tell an auto-dialer to place a pause while dialing. This isn't the type of number you send a person, but the type of number used for a mechanical call from overseas to the U.S., and possibly the only type of number the writer of the email has ever seen.
So what would happen if you did write or call them? You would most likely get a very helpful employee on the line who would apologize for the error and offer to fix the matter right away. All they would need from you is your bank information to reverse the charges.
Stop — full stop. Never, ever give out your bank information to an unknown source. With those numbers, they can completely drain your account. Keep in mind, that if you do get connected to people running these scams, they can be very forceful in their delivery and make all sorts of threatening accusations. You will never be wrong to hang up, go to the actual company website, and find the number for the real customer service.
As for the banking variation of this scam, real banks resolve fraudulent charges differently. Suspicious activity with an actual bank would normally put on hold or cancel the transaction unless you tell them it is expected. If you don’t contact them, they won’t put through the charge. When you receive an email stating “We will put through the charge unless you contact us,” it is usually a scam.
The reason for this is banks will have to pick up the cost of putting through a transaction that may be disputed, particularly if they know the transaction is illegitimate. The same is true with credit cards. According to the federal Fair Credit Billing Act, as a fraud victim, you are only responsible for the first $50 of a fraud charge, and your banking institution has to pick up the remainder. Many banks have also extended this protection to any account that uses an ATM card. The law provides incentives for the bank to install software that helps flag suspicious charges. It is also good customer service.
Receipts for antivirus computer software, such as this one, are particularly dangerous because the scammer may also tell you that they have to check your computer. They will happily walk you through the process of allowing them to remotely connect into your machine so they can verify that you have the correct software installed.
At DCMA, we often do this for our work with the IT help desk. As a result, many people think it is legitimate. It is not. Once inside your machine, they have control of everything stored on your computer.
They can also install ransomware, a virus that will shut down your machine completely and require you to pay money to get access to it again. This dangerous situation will lock down your computer records, pictures, email and everything else, and to get it back, you will have to pay.
This is a type of virus that can also be installed by clicking a link in an email. When ransomware was first used, there were several hospitals employees who clicked on some email links, which installed a virus into the hospital network. The virus locked up all of the hospital records. Doctors could not get to patient records, files that recorded medication were inaccessible, and lives were endangered. Ransomware on such a large scale drew attention and significant repercussions, so the thieves moved to smaller targets, like you and me, in hopes of doing a volume of business unlikely to draw a lot of attention.
So, as always, keep in mind a few simple rules:
- Never click on a link inside an email.
- Check the email address.
- Go to the companies page and look for the customer service address.
- If you don’t recognize it, assume it is a scam and examine it carefully.
- Never be afraid to hang up on a suspect call. Call back using the number on the company website, not one in an email.
I still like shopping online, but I'm careful about receipts. Keep these rules in mind, and you can shop safely online too.
Until next time, stay safe out there.
Read more from this series on Online Safety:
Online Safety Tips: Spot the Scam > Defense Contract Management Agency > Article View (dcma.mil)
Spot the Scam: Phone Fraud > Defense Contract Management Agency > Article View (dcma.mil)